Understanding the basics
Ransomware is a type of malware that blocks access to data or systems unless a ransom is paid and threatens to publish it, Some Ransomware has a deadline. If the victim fails to pay up by the deadline then they may lose the data. Most exchanges are done via Bitcoin.
Ransomware is a rapidly increasing threat to the data files of individuals and companies. On an infected computer, it encrypts data and retains the key to decrypt the files before the user pays a ransom. This malware is responsible for damages of hundreds of millions of dollars each year. Due to the large amounts of money to be made, new versions appear frequently.
Mechanics of Ransomware
There is a very compressed timeline of an attack. From exploitation and poisoning to getting the ransom note, you frequently have 15 minutes.
Step 1: Infection-Ransomware is downloaded and installed on the computer secretly the most common way of sending ransomware is phishing mail.
Step 2: Execution-Ransomware searches and maps locations for targeted types of files, including locally stored files, and network-accessible mapped and unmapped networks. Any ransomware attacks also erase all backup files and directories or encrypt them.
Step 3: Encryption-Ransomware uses the encryption key to share a key with the Command and Control Server to scramble all files located during the execution step. Access to the data is also blocked.
Step 4: User Notification-Ransomware adds instruction files that detail the method of pay for decryption and uses those files to show the user a ransom note.
Step 5: Cleanup – Ransomware normally terminates and destroys itself, leaving behind the instruction files for payment.
Step 6 : Payment: In the payment directions, the victim taps a connection that brings the victim to a web page with extra details about how to make the appropriate payment. To prevent detection by network traffic monitoring, secret TOR services are also used to encapsulate and obfuscate these messages.
Step 7 : Decryption: The victim will obtain the decryption key after the victim pays the ransom, normally from the Bitcoin address of the offender. There’s no assurance, that the key will be delivered as promised.
Types of Ransomware
There are primarily two kinds of ransomware:
- Locker Ransomware – Ransomware from Locker denies access to computing services. It is based on blocking access to a computer such that it is difficult to access the GUI. From there, it prompts payment by users to unlock the unit.
- Crypto ransomware – Crypto ransomware denies access to files on the computer. It’s possible to access the user interface on the computer, but the files can’t. By encrypting the files and requesting payment for decryption, it does this.
Examples of Ransomware Attacks
CryptoLocker
Cryptolocker was one of 2010’s first global ransomware attacks; it infected more than 500,000 computers at its peak in 2013 and 2014. A botnet, distributed through spam email, was used to encrypt user files. Overall, CryptoLocker harvested around $3 million with its variants taken into account.
Teslacrypt
Gamers were aimed at TeslaCrypt, capitalizing on the importance that devoted users put on files such as saved maps, sports, and material for downloadable video games. For ransom, it encrypted these files. Interestingly enough, the attack developers ended up releasing the encryption key publicly.
Simplelocker
SimpleLocker is one of the first smartphone ransomware attacks on a wide scale. It encrypts mobile files through a Trojan downloader, targeting Android users.
Wannacry
One of 2017’s most notable attacks, WannaCry has raced across the United States and Europe, affecting hospitals in particular. A noted Microsoft vulnerability known as EternalBlue took advantage of the attack. Although the patch was released, many systems were unable to implement updates and were left vulnerable, leading to a high volume of infections.
Is there a way to avoid this?
Preventive mechanisms
Proactive approaches are a must when it comes to preventing ransomware attacks. An organization needs to plan to stop a computer infection, similar to immunizing yourself from a physical virus.
Update Security – New variants of ransomware are regularly published. Safety tools and operating systems are continuously modified to prevent becoming the target of the latest upgrade. Upgrade any obsolete and unpatched applications and keep up to date on anti-virus rules and signatures. Do not make the work of cybercriminals easy.
Bolster Firewalls- To distinguish and evaluate different kinds of network traffic, firewalls are used. Data is provided when ransomware attacks are publicized to help filter out the threat. In WannaCry, for example, the call was to directly reject all (TCP) Port 445-SMB, (UDP) 137, (UDP) 138, and (TCP) 139 traffic.
Back up your files regularly and frequently – The harm caused by a ransomware attack can be greatly reduced by getting vigilant data backup processes in place, as encrypted data can be recovered without paying a ransom.




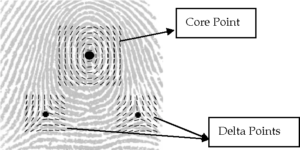 Type Lines-
Type Lines- Bifurcation(Fork)-
Bifurcation(Fork)-